Let’s consider a case where you have limited disk space available in your database server. In addition, you need a database backup quickly. However, you estimate that, the space available in the server for the backup is not enough.
Continue readingLinux
MySQL Utility – mysql_config_editor
These days most applications use some kind of database service to store data. Also, It’s important that this data is accessed securely. In that regard, this article focuses on MySQL database service and more specifically on the mysql_config_editor tool.
Continue readingAdd EC2 Linux user using Cloud init user data in AWS
Consider a scenario where a customer has provided you with an access to a AWS console and needs you to recover a running EC2 linux instance for him. Let’s assume that the customer is not very tech savy and not in possession of any private keys to the instance.
You got two options at this point in gaining access to the instance and working on restoring the system.
Continue readingRemoving Pre-Routing NAT Rules in IPtables
To remove specific iptables rule from Pre-Routing chains, first display all Pre-Routing chains using a following iptables command:
iptables -t nat --line-numbers -L
This will display all Pre-Routing chains with relevant line numbers. To remove a specific Pre-Routing rule, you can use the corresponding line number. For example below command will remove Pre-Routing NAT chain with line number 1.
iptables -t nat -D PREROUTING 1
ipsec VPN tunnel between local private network (pfSense) to AWS private network (Openswan)
Scenario: A local private network and a private network in Amazon Web Service (AWS) needs to be connected securely over the internet through an ipsec VPN. In order to cover an expanded scope, VPN tunnel will be established between Openswan ipsec VPN from AWS to pfSense ipsec VPN in local network.
Main AWS VPC in this scenario “172.31.0.0/16” has 2 subnets, Backend (172.31.1.0/24) and Frontend (172.31.2.0/24) respectively. Application servers are hosted in Backend subnet while Openswan VPN server is hosted in Frontend. All traffic between these 2 subnets are allowed.
Continue reading
Apache access to Network Database on Custom port
If you have an Apache (httpd) application that needs to access a remote Database, you will have to change the SELinux policy as described bellow to allow Apache access to network databases. You have to edit the SELinux boolian settings for this.
First, check if the “httpd_can_network_connect_db” boolian set to “on”.
[root@testsrv ~]# getsebool -a | grep httpd_can_network_connect_db
httpd_can_network_connect_db --> off
By default, this is set to off. To enable network database access for Apache, execute bellow command.
setsebool -P httpd_can_network_connect_db on
Note, that “-P” is added to permanently change this setting therefore on system reboot this setting will be preserved.
If the database that the application is trying to reach is other than the default port (eg. mysql: 3306), you have to edit the SELinux Policy as described bellow.
Assume the application trying to connect to a mysql database and custom port is 1234. To get the current settings for mysql in SELinux policy,
semanage port -l | grep mysqld_port_t
To add new custom port to this mysql port group,
semanage port -a -t mysqld_port_t -p tcp 1234
Later on if you need to remove any custom port that entered in a port group, (eg: mysql:1234)
semanage port -d -t mysqld_port_t -p tcp 12345
Change permissions of files, folders and sub-folders in linux
Let’s assume we have a folder /opt/docs/ and we have to create bellow folder tree, which are used by Accounts, HR and Sales divisions. Each folder is accessible to respective devisions only and others must not have any access to it.
/opt/docs/
|-- Accounts
| `-- Employee
|-- HR
| `-- Employee
`-- Sales
`-- Customers
To make the folder strcuture,
mkdir -p /opt/docs/Accounts/Employee
mkdir -p /opt/docs/HR/Employee
mkdir -p /opt/docs/Sales/Customers
To change ownerships to respective divisions,
chown -R accounts:accounts /opt/docs/Accounts/Employee
chown -R hr:hr /opt/docs/HR/Employee
chown -R sales:sales /opt/docs/Sales/Customers
To set access permissions only to respective divisions,
find /opt/docs/ -type d -exec chmod -v 0770 ‘{}’ \; # directory permissions
find /opt/docs/ -type f -exec chmod -v 0660 ‘{}’ \; # file permissions
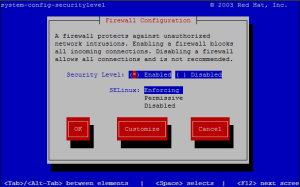
Configuring Linux Security level and Firewall from Command Line
If you need to configure the Security level and firewall of your Red Hat system and you only has a SSH access to the system, use bellow command as a privileged user.
system-config-securitylevel-tui
Configuring SFTP CHROOT service
Let’s consider a situation where you need to configure a secure FTP service in your Linux server without installing any new packages to the system. Easy way of achieving this scenario is by configuring a SFTP CHROOT service in your Linux system. By Default all Linux systems are pre configured with SSH service. There for you only need to edit the existing configuration for this purpose.
1) Modify “/etc/ssh/sshd_config” file to reflect bellow changes
#Subsystem sftp /usr/lib/openssh/sftp-server
Subsystem sftp internal-sftp
Enable multiple users Read and Write permission for files within a folder
Lets assume we have two web developers working on the same web project and they will need a single shared location to store and collaborate their development work with each other. In bellow example I have taken “/var/web-dev” as the shared location and it’s owned by Apache user (www-data). Two developers, danny and penny, needs to store their development work in “/var/web-dev”.
Assuming we already has logins for danny and penny, we have to add them to Apache user group.
usermod -aG www-data danny
usermod -aG www-data penny